Since the 2000s, Aubrey Cottle has been the owner-administrator of 420chan.org which, until recently, was one of the most popular chan-style imageboards online, second only to 4chan or its Japanese inspiration, 2chan. His name is kirtaner. Pronounce it however you want to.
Life carried on somewhat peacefully, without major, life-ruining incident for what were undoubtedly many fun years of friendship around 420chan. Kirt was a successful businessman, making up to $3,000 a month in ad revenue, married and father to a new son. But in the next few years, kirtaner would slowly burn through his friends, family, and community, all to destroy his own website for minor internet fame, while ominous figures whispered to him from the shadows.
What began as an interview on Hate Radio in which kirtaner announced his status as official Founder of Anonymous – a dubious claim to notoriety which he later retracted – kirt’s meteoric appearance would burn bright, flashing marching orders onto the screen, calling together all the old heads from every corner of the Internet for “one last job.”
It was a moment of almost frenzied optimism, half a year into the COVID pandemic. The call to action was such a revelry, coming from the unexpected heights of Mt. 420chan, that for a moment, every sensitive ear was listening in eager anticipation of who was attempting to revive Anonymous now, all these years later, and to what end?
Kirt’s enthusiastic audience tuned in. 420chan users lit up the chatroom with memes, cumdogs, dicks everywhere, and some insightful discourse around the danger of irony.
Executive creeps listened. Regular creeps listened. Jake Davis listened.
Tech industry leaders caught the podcast from inside their Teslas during the drive time commute.
It was a moment when Kirt had everyone’s attention, and he was having fun with it on Hate Radio. He even took a bathroom break so he could have more fun. Extra fun.
Hate Radio is brought to you proudly by Lebal Drocer, Inc. which must never be shortened or abbreviated, and contractually obligated to be spelled out in full, in every instance, hyperlinked if possible, or risk severe legal penalties. Tell your friends!
The air was jubilant with hope. The internet activism machine was spooling up, once again whirring to life. Many 420chan users were happy to see the community featured on a hateful little podcast. IRC was popping with life. Signals lighting up. It was a party all around. In the wings, however, Kirt’s closest friends expressed concern.
“This is not going to be good for him,” one said after the show. Another said they’d seen something similar, but a smaller episode. This was something new, they said, and about to be bad.
Kirt told the world there would be a great big old hack a comin’ round the bend, and y’all just go ahead and start logging in, now, on this Element server he created for the purpose.
The questions on everyone’s minds in the server:
Who was the target? And how?
The air was quiet, punctuated with occasional jokes and threats against the Man. It had the feeling of being on the world stage, and a smoky backroom at the same time. For a few moments it felt like 2011, the promise of revolutionary hacktivism once again buzzing and vibrating, front and center.
But it was not long before the air soured with the smell of something off—the unmistakable feeling that something was wrong in the Element server.
Because of its high-profile appearance as THE place to come and do cybercrimes together, it took on the familiar shape and identity of AnonOps IRC, once flooded with young people in 2011 who would soon be put in prison for doing their part.
Script kiddies and young hackers first flocked to AnonOps that year with a promise of a shortcut to rockstardom, as well as Project PM. They were funneled directly into the hands of law enforcement, eventually leading to arrests.
Hatesec asked Barrett Brown in May 2011 why he was inviting naive kids onto a server where he knew actual agents on the federal payroll were likely hanging out. Shortly following his announcement in 2020, Jihad of wtfux asked Kirtaner the same question, expressing concern that they were openly discussing their crimes on discord, offering little to no protection to the identities of anyone involved. Both times, these concerns were dismissed as efforts to undermine the important work of hacktivism. Jihad must be a fed, the line went, and hatesec was only trying to make a prank call.
Come one, come all. We got federal oversight, police joining in. CIA rubber stamp: totally safe!
As predicted, Kirtaner brought on the same problems for his group as Brown did in May 2011.
In fact, Kirt would soon partner with Brown, even hosting his ongoing Project PM conversations, using computers given to him by Nerdy Rauhauser. This is where the story gets muddy.
[Editor’s note: This claim was posted by Kirt in the hate radio discord channel. More on this later. For now, be advised that Neal Rauhauser is the shit that once stepped in, never comes off your shoe. His name is mentioned throughout this piece due to obligation, because as you will notice, he forces his way into stories where vulnerable characters like kirtaner are seen forming state enemies. Neal, like other figures in this story, is a predator. It serves his image as some kind of intelligence or security analyst, whatever he claims to be, to be associated with these subjects – whether the press is negative or positive – and it is for that reason Internet Chronicle disrespects his name in each unavoidable reference. If you are reading this because you googled him, perhaps in the search of supporting evidence that Neal Rauhauser is good at security and intelligence (or whatever his claims are), or that he is perhaps someone worth being involved with, you will not find that assurance here. After a decade of monitoring this person’s activity, there is no evidence that Neal R. has any actual talents, certainly nothing with regard to charm or personality, and his success appears to be entirely contingent upon the stupidity of others and their willingness to self-own. Read on.]
One would think that seeing so many fall to their deaths after attempting to take the hackerman shortcut to becoming a LEGEND OF INTERNET LORE, that Aubrey Cottle – who has seen it all – should know better than to try to stick his own dick into the third hole on the farmer’s barn door. But nah, he actually went for it. He was horny for it.
Months went by, and the substance was still lacking. Apart from some small successes, it seemed maybe there was nothing to that whole operation, anyway. Nevertheless, Internet Chronicle was scoring major strikes to the upper echelons of the real-life pedophiles controlling the QAnon conspiracy, while Kirt was packing his 420chan discord full of hackers in what would become only one move in a long string of bizarre decisions which would destroy the forum, and Cottle. But Just as the ewoks were finally losing hope, there it was! A smoke signal on the horizon, a hack attack happened, everyone clapped, and consequences were never the same.
Every Deleted Parler Post, Many With Users’ Location Data, Has Been Archived
The ol boy was no bullshit, afterall! By gum he hacked the ever loving shit out of that FUCKING WEBSITE and it was KILLERRRRRRRRR.
Not long after its establishment, the Element server was taken down, as well as the IRC server, and you can see where this is going. Currently there is no operating 420chan.org server, and the last time it was fun was two years ago, when it moved to discord, before losing IRC altogether.
To an outsider looking in, this could easily be explained by the sudden criminal overtones of 420chan’s new attitude. No longer were Kirtaner and others laying low, smoking weed and laughing about wrestling. It was wartime, and websites could be expected to go down. Kirtaner devotees could even perhaps overlook the loss of 420chan as a necessary casualty in a righteous fight for justice, in their blitz against QAnon.
Still, something felt off. What was happening in public, and affecting the 420chan userbase, did not jive with the longstanding uptime of the imageboard’s history, or that of the IRC channel. Critical minds began to wonder, how could such a capable sysadmin lose control of his assets in such a short time? Did he not see this coming? Was the heat really that bad?
A person’s character is revealed by how he responds to stress.
Kirtaner, the ego of Aubrey Cottle, demands constant external validation. Call that Aubrey Coddle. This grotesque character trait is the doorway to peril. Kirt’s constant need for approval from high places is one characteristic that, when combined with his need for immediate gratification, makes a person ungovernable, even by his own volition. He is subject to whatever is in his face in a given moment, and to even hold his attention requires a song and dance, and commitment to personal involvement, that only an equally crazy person can sustain. This would be his undoing.
Peas in a Pod
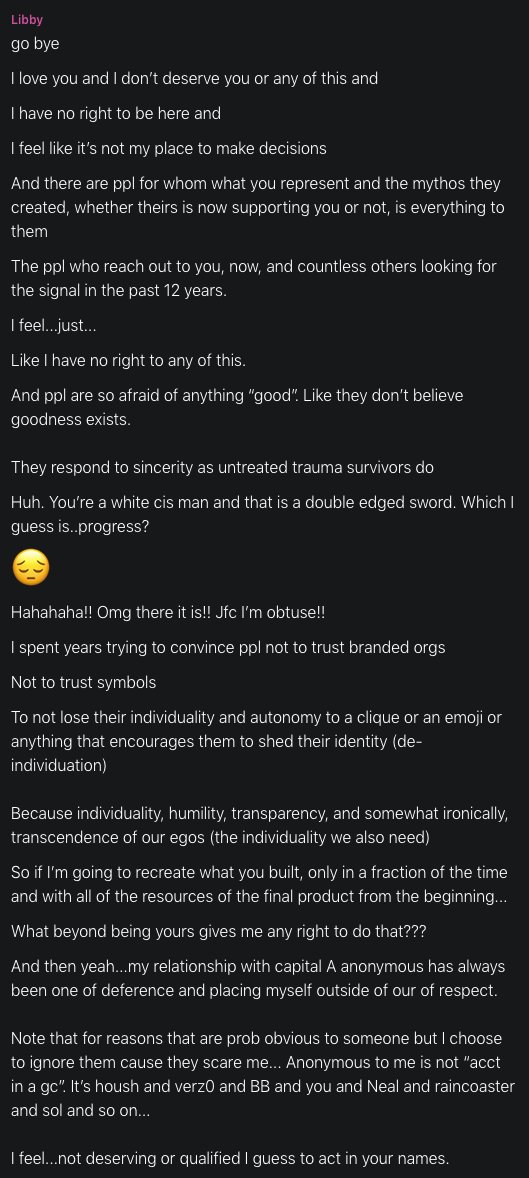
Following closely behind Kirt’s sudden, high-profile flash into the public eye, was a figure in the smoke, a new face nobody recognized, saying she’s close to Kirt. She is a brunette named Libby Shaw. Talks big. Righteous and pure. Hates mean people. She said they had already been talking for a while. Publicly, they seemed madly in love.
Meanwhile, Kirt’s child with another woman – his wife – was on the way.
Although a bit sloppy, it has always been this fun, silly, and admittedly murky puddle of hackster culture that created the merry moments of LulzSec, or the sweetness when Hal Turner’s life crashed in on him, or the worldwide hilarity of seeing Westboro Baptist hacked live on international television…And who can fault anyone for being ugly sometimes? So everybody thought, ‘Fuck it! Thanks for the free computers, Neal,’ and dove right on in.
People chasing the high times of them good old days quickly noticed that this ride felt different, and yet eerily familiar in its trademarks. The playbook, with its yellowing pages, and tattered edges, had begun to show its age. Drugs did not make anyone younger, either.
After hosting Barrett Brown’s Pursuance software, Kirtaner is said to have stolen the source code and repurposed it to fuel Libby’s “Internet Hope Machine.”
This vanity project by the love of his life turned out to be another doomed, bullshit attempt to offer a more sustainable and tame version of Anonymous, a form of Anonymous that ‘moms like you’ can safely get behind, and likely burned a lot of bridges in its implementation.
It was not completely useless, however. In fact, if she were smarter, it could have ended up serving as a brilliant entrapment scheme to keep records of every action taken by members of a criminal conspiracy, forming around their burgeoning Bonnie and Clyde mythos. Libby Shaw is a strong manipulator, but she is not organized in the least.
~Trigger warning: Ugly abusive person below~
But first, a message from our sponsor:
THE ALL NEW LEBAL DROCER LOVE MACHINE IS A SUBSCRIPTION BASED SYSTEM THAT SHROUDS THE UGLY INSIDE YOU BY EMPHASIZING WHAT’S LEFT OF YOUR YOUTHFUL BEAUTY.
Join now and Lebal Drocer packaging robots will include a rare, limited-edition skin care package to get rid of those unsightly dark circles under your eyes. Lebal Drocer understands that whatever you did to earn those sunken bags under your eye sockets put irreversible pits in the soul. Not to worry, you can still lose the permanent dead-eyed lich-face, with Lebal Drocer LOVE MACHINE EYE MASK AND SKINCARE ROUTINE.

An unfortunately familiar face
Libby Shaw and Kirtaner told Internet Chronicle that somehow they managed to get big-shot Internet man Negative Rauhauser to send over some powerful servers to help facilitate his new work in activism. At the same time, fun reports indicate that Rawhoser had installed a miniature Van Eck phreaking device for intercepting side-band radio waves from kirt’s 15 monitor setup, a completely untraceable method of surveillance.
[Editor’s note: yo dawg we heard you liek conspiracies so we put a conspiracy in your (conspiracy~]
Wouldn’t you know it? Internet Chronicle was on the scene. Did you see that coming?
No seeds. No stems.
It’s dank journalism
and we are giving it away for FREE
Like Libby, N. Rauhauser is a recurring character who – for some reason – wants to make connections with susceptible personalities. If high-profile online personality disorder blowouts were all different Final Fantasy games, Rauhauser would be Cid, and he flies on an airship powered by raw insecurity.
Neal, like Libby and other predators, would appear because Kirt’s successes were undeniable: In October 2020, Kirt claims to have been an anti-QAnon researcher exposing connections between Jim Watkins (confirmed by Chronicle to be the author behind QAnon) and domain names connecting Watkins to child pornography.
In November Kirt claimed responsibility for exploiting security flaws in right-wing social media platform Parler. This would lead to the exposure of an email newsletter database, making international headlines and having far reaching implications on the ability to bring justice to the Brown Party wannabes behind January 6.
 Seeing that it was imperative to cling to these successes, Shaw made it her purpose to get involved and be allowed to claim her spot in history as an “intelligence analyst” and researcher credited in August 2021 with exposing the developer behind QAlerts, an outlet for official Q posts.
Seeing that it was imperative to cling to these successes, Shaw made it her purpose to get involved and be allowed to claim her spot in history as an “intelligence analyst” and researcher credited in August 2021 with exposing the developer behind QAlerts, an outlet for official Q posts.
Readers familiar with patterns of narcissistic abuse will recognize the textbook methods Shaw used to make Kirt dependent upon her.
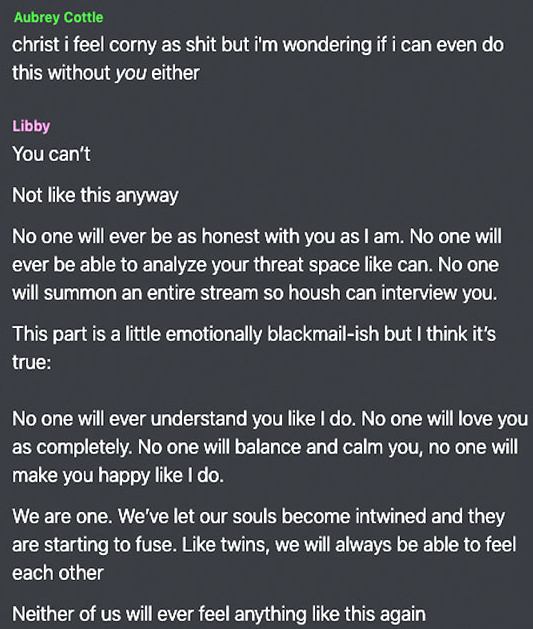
It is no wonder that Kirt’s explosive entrance onto the main stage of Anonymous was followed shortly thereafter by strange manic episodes.
If LulzSec, or Greenman Anonymous was the 1960s free-love movement of trolling, the Kirtaner revival of Anonymous resembled the heroin-soaked stormcloud of the 1970s, rolling in behind.
Kirt’s strange behaviors took on the forms of frenzied mumbling, whispering videos threatening Barrett Brown, resembling full demonic possession.
Pressing a knife up to his throat last summer to defend Libby’s honor – again, perfectly normal behavior here at the Internet Chronicle – was good, wholesome fun everyone could get behind. His threats of suicide were reminiscent of the good old days, when Topiary would go online and threaten to hurt himself or others. Suicide trolling, the oldest troll in the book. Jolly good time innit. That’s just good comedy. It was remembered by critics as the funniest threatening self-harm committed to video since that monk failed to light himself on fire on America’s Funniest Home Videos, with Tom Bergeron.
As thousands stood by, monitoring the spectacle, many have asked: What fuels that furnace of ambition?
Behind every great man is a great woman.

A cynical Machiavellian acting in all modes to – for some reason – increase her online power, Shaw deployed a sustained pattern of love-bombing, intermittent reinforcement, lies, abuse and coercion.
Although it does not absolve her of any guilt (or Kirt, for that matter), it is worth noting that Shaw herself is merely one link in a long chain of hate and creepy interactions. The link adjacent to her, for whatever reason, appeared to be Neel Rowhouser. For reference, links ahead of Shaw do not appear to be real people with souls and livelihoods, but instead resemble the cloud of online personas circling Neal. The difference here is that the accounts supporting Shaw appear to be relatively fresh Twitter accounts, that speak only to this niche subject matter, with first follows that begin with other accounts in their circle, usually the same person, and revolve around an increasingly small circle of names, as the flesh and blood human beings who are willing to be involved with Shaw, Kirt, Neal and others, has all but completely shrunken away.
Consensus online is that Shaw acted as an intermediary brain-sucking vampire. Once the living will was drained from Kirt, demonic influences from the void space between stars – the cold background noise of hateful entropy – naturally began to take hold of him. The darkness was winning. Hyperbole aside, these people can and do kill their victims.
Everything Neal, Shaw and Kirt touched would begin to shrink and wither, day by day. From the start, 420chan was doomed to a slow death.
But at first, Kirt was posting his cock to his 420chan discord, dripping precum and ready to rock, fucking the very internet itself. He went in raw.
Mosquitoes were swarming around him, feeding on his cockblood. His skin was supple and white, hidden from the daylight, kissed only by the glowing wall of display panels. His boyish freedom, apart from his responsibilities, was there for the taking. Tender and sweet. Predator meat.
Openly committing crimes, whether computer or otherwise, invites a criminal element. Predators looking for prey. They can spot an ego-mark from a mile away, and here before Shaw was a baby manchild, with big starry eyes, a Gordon Ramsey smile, and a dream in his heart—also, a nasty lust for extramarital pussy.
Whatever it took, she would have him. But that would not be enough to satisfy her need for control.
On went the sexting, and gross videos, and real life meet-ups, right in the middle of while Kirtaner was trying to shake shit up online. The harpy came a rapping. His wife, with child, stood behind him, wondering, ‘what will happen to us?’
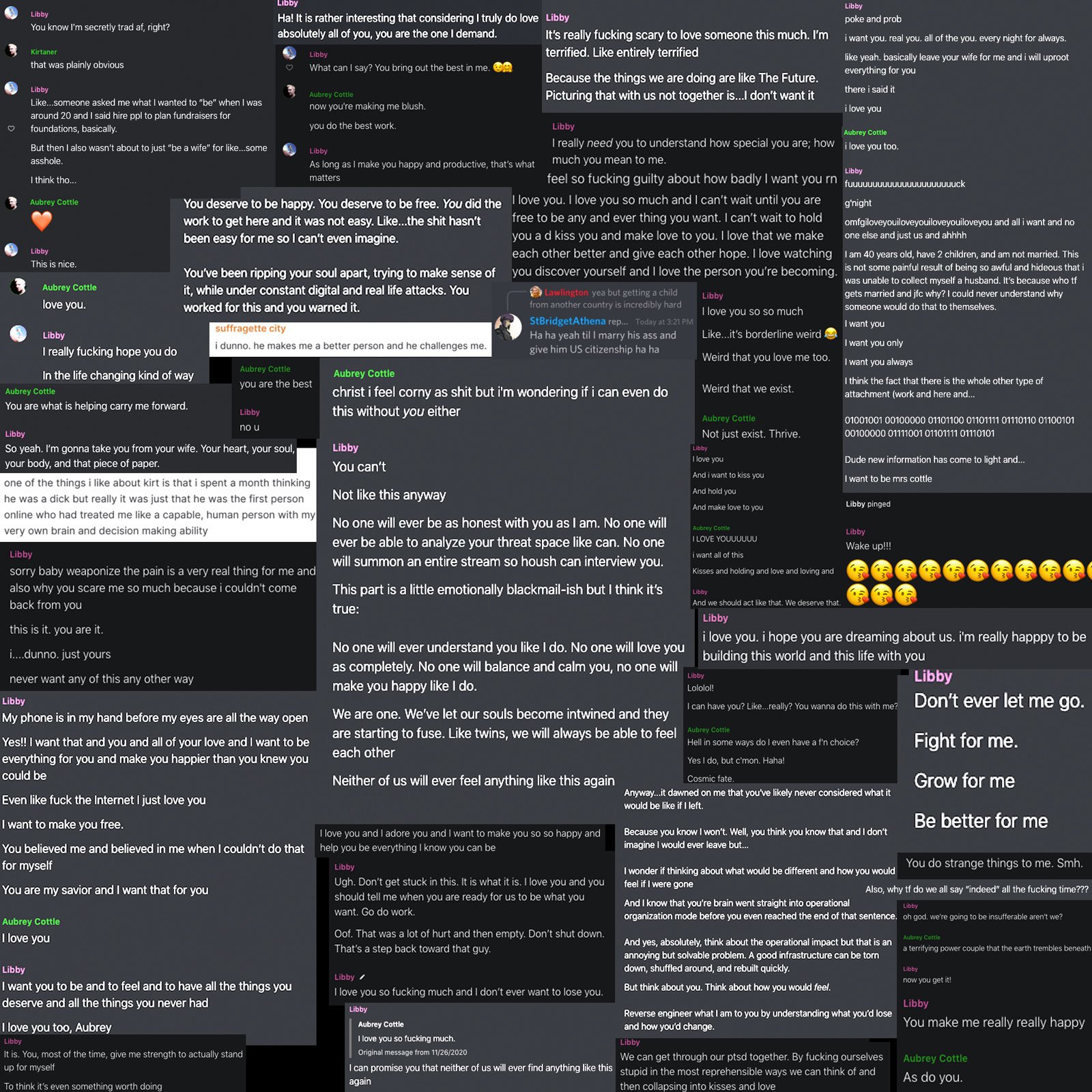
Shaw would have to tear him from his wife and son by offering Kirt the only thing she could offer: The most deeply manipulative and toxic relationship the Internet has ever fucking seen! Moreover, Kirt would have to be receptive to such a scheme.
ELECTROCHEMISTRY [Medium: Success]
“Fuck this family.”
Medium: 10
vs
Your Total: 11
Got to get that stinger wet, son! *This* is the digital future that was promised to you.
Kirt shot for the destiny he felt he deserved. A lot of nasty people go after power just for power’s sake, or fame just for the sake of attention. Kirt is no different. He is an abuser and a manipulator. He is no one’s friend. Kirtaner is a destroyer in name and in spirit, and with that, you get what you give.
He might have a mental problem that prevents him from having empathy, and/or kirt’s decline is the outcome of getting played by con-artists. He could also just be a colossal piece of shit underneath all that. Something was driving away his friendships, though, same as it drove him to become a magnet for “fun, illegal” activity, but looking like it came from a rather dusty old playbook that everyone but Kirt seemed to recognize.
To wear the mask of Anonymous burns the wearer’s face and skin. It bonds to the flesh. Suddenly the eyes of every fed and defcon attendee are on you, and they are COMING. The FBI can feel the call of any Guy Fawke’s mask. Confiscated masks are used as a currency for trading favors and contraband, as well as worn ceremonially in ritual baths.

After assembling all the do-good hackers on the internet into his discord, kirt banned the word “retard”. Daily arguments broke out between the “blue name” hackers and the original 420chan community. Illegal behavior was being openly discussed, causing an atmosphere of constant tension and panic for those who were only there to enjoy the high quality memes. Eventually, Libby was granted full administrative control over all 420chan servers, and the site lay in ruin.
40 oz Gorilla, a 420chan administrator, destroyed all the chat rooms in the 420chan discord, permanently deleting many years of community discussions. He’d also been burned in a fake relationship with Libby.
“It just wasn’t chill anymore.”
Nigel Haggledicker, former poster at 420chan.
People cared deeply about the site, and were sad to see it go down. Having destroyed their shared passion, how could they care, now, that kirt, too, was going under? What could even be done to save him? Kirt was not interested in saving himself. So his friends went away, because they had already been driven out by the tension, rallies to egomania, or just by kirtaner himself.
What’s left for kirt is a group of individuals that is only satisfied when they are doing harm. Making an impact. Writing ‘lololol’ to each other like coyotes, yelping around their victims. Now, they are snapping at him.
To interact with any of the internet goblins in the nealhause cult of ruination is to engage with them all. It is to become trapped in an awful slime. A carnival where all the rides are spinning at 50,000 rpm, liquefying the brains of anyone who wants to take a ride.
The actors, however many or few there are, share a pattern, attitude and sensibility, and travel like a school of fish. Mention any character attached to their bullshit, and they will dart at you, their toothy little mouths picking you down to a skeleton, if they can.
They write in a bubbly fashion and their auto-generated usernames are flush with emojis that make no sense at all. They type in a childish, irritating manner, using ? emojis to laugh at their own tales of name-calling. Most noticeably they quickly try to involve themselves in exactly who you are.
“What was that link you shared in the gc?” Shaw asked Chronicle writer hatesec in November 2020. “It was a playlist you made on your personal youtube, what was that link again lololol i dont want to have to scroll allll the way back up ?”
“Five times, Shaw pressured me for that link containing personally identifiable information. This, after sending me a video, unprompted, of herself rubbing one out on camera. Fortunately, I have a third-world phone plan that degrades video quality to the point that I only had to interpret the general idea of the heinous sex act she threw in my face. That youtube link to my personal playlist was an important key to who I am as a person, and she was clearly after it. Why me?
Even during that time, when I was in the thick of my own inner pain, I realized it was because not only do I have the privilege of writing for Internet Chronicle, and running Hate Radio, I was also visibly injured, and talking publicly about an abusive breakup I was enduring. This is a clue for predators, a sign that one can be violated.
She said I needed to get over that narcissist – I immediately recognized the irony – and she said that maybe some pussy might help me get over it faster. She wanted to go to the next level, and meet up. She said she wanted to FUCK. I scanned my room, looking for the obvious things I would need to hide before her arrival – notebooks, laptops and hard drives – and I called her bluff. I said sure. Come on out.
‘Isn’t she with kirt?’ I thought. ‘Maybe they’re doing some kind of open relationship thing?’
Or maybe she’s just a whore, I thought. I knew Kirt and I were not the only ones. Regardless, it was the kind of boundary overstepping that I had come to recognize as straight up insanity, so I took note of that. I pressured her to come out early, knowing she’d cancel, and I did not ask to reschedule.”
—hatesec
Each person orbiting in the aforementioned creep cloud is the same in their excessive use of emojis, usually following some basic mom-take shit that’s not even Facebook-funny. But the biggest tell is that they don’t actually know how to have fun, and that’s always a good way to spot someone who is bound to ruin your fun happy time.
These people can not read the room. They can’t tell when they are creeping everybody out. They are just grotesque, and they often do not realize when people are taken in by them, versus when they are just standing back, and letting them be crazy, without interrupting, and simply watching the freak show for what it is.
If you are a human baby manchild like Kirt, though, you wouldn’t notice that sort of thing. A set of car keys jangling out in front of Kirt would have been enough to distract from the fact people were barging into his life and dismantling what he spent his younger vitality building. For what? A little pussy? Some clout online? Fine, be asleep at the wheel.
A series of overlapping egos online, the ruin of Aubrey Cottle is trailed by Libby, who is next, and in the static, an older, aging face. The pale, flickering image of a full-time creep emerges from a rendered fog. It is N-word Rauhauser, again.

How are you not tired of this shit, by now? What demons stand behind you?
Give it a rest. Age gracefully. Disappear. Quiet your mind.
These are fantastical suggestions to some. Impossible tasks. The shared sickness that gets in the way of true spiritual fulfillment, it binds these toxic personalities together in a shared race, each jockeying to be meaningful, to make an impact, to make a change, whether harmful or benevolent, THEY are making a BIG DIFFERENCE.
There’s no money in it. There’s little to no sexual payoff. There’s no career advancement opportunity. So why are these people so intent on being there? Who are they?
They’re nobodies. But next to Kirt, they are somebody. The story is really that pathetic.
All these associations can really make your head spin, but keeping it in the simplest terms without harming accuracy is helpful in following the logical procession of bullshit: If the chain of abuse goes backward from Libby to Neal, then what’s ahead of Libby? In this story Kirt is the obvious object of her abuse. But Kirt’s doing great things on the world stage! He’s attacking QAnon! Are there any actual victims ahead of Kirt?
There is a wife and child, who is already without a dad. Throughout their entire adult relationship, Kirtaner’s wife suffered physical and emotional abuse at the hands of his personality disorder. As early as 2008 there have been reports of Kirt physically hurting his wife.
Hatesec first approached kirtaner around 2011 seeking to purchase advertising space for the site on 420chan. The emails went ignored. A short time later, when hatesec responded to rumors on IRC that Kirtaner was physically abusing his wife, Kirt finally reached out, contacting hatesec for the very first time in their lives, only to ask him to take down tweets containing the allegations of abuse, stating via DM that they were not true.
Later, in 2018, Kirtaner said it would be fun to go on Hate Radio and talk about the good old days. Two years later, he asked again to come on the show, and hatesec finally agreed. Until now, those allegations never came up again.
Kirtaner’s wife and mother of his child, spar, often kept 420chan’s servers and boards going while kirt was distracted or busy, and was an active member of the community.
In the years leading up to his downfall, spar would become the target of Kirt’s continual spin, manipulation, and abuse. Screenshots from their private conversations were dropped into the 420chan discord regularly, to some of spar’s best friends. By this time spar was of course banned and no longer present to defend herself. Kirt’s obvious abuses of power were frightening the 420chan community and silencing the fun banter, sometimes for hours. Regular posters became increasingly tired of Kirt’s distortions.
Spar alleges many abuses, physical and psychological, including the menacing of her mother and their child, as well as the unfair control and mistreatment of their family pets.
It is precisely because of how much Kirtaner has lied about his past, his associations with Libby Shaw, Neal, and more, that even his downfall has cast doubts.
Having so many lies and transgressions on his record now makes it equally difficult to believe that his computers were actually seized on Tuesday, in association with the Epik hack.
Kirtaner raided, computers seized

By the look on his face, they probably were.
Are you all used up, yet, Kirt?
People with humanity have, for more than one year now, hoped that Kirt would get offline for a while, put his feet in a cool stream, and reassess what life is really all about. Not everyone is enjoying the trainwreck. Most people just want to see him take a step back, work on himself privately, and do right by others.
Unfortunately, comeback stories rarely take place on a useful timeline. His wife will eventually learn to love herself again, and move on, with therapy and without Kirt. His son will most likely never have a meaningful relationship with his father, and if he does, it will be awkward and marred by the earliest instances of rejection and twisted abuse from the man who helped bring him into the world. There can be no Kirtaner comeback. With therapy and guidance, Aubrey Cottle can possibly emerge for the first time, and embrace traces of his own humanity, if they exist. Still, this helps no one in the short term.
Libby Shaw’s getting hers. People who originally supported her are awake to her bullshit, but only for themselves, and claiming to have been lurking, or spying, or some other self-serving explanation, all of which lack the awareness that the best course of action is to get out of the game altogether. They think they are scrapping together some picture that says, “I meant to do that,” but they got played, too.
Neal fades into the background. He will be another 10 years older when the next head of the hydra comes out to play again, and through sheer will, he will find relevance again, somehow. With one bony hand in his pocket, and the other throwing up a peace sign, there he’ll be, surfing in on the next big wave of netscape nihilism.
All of these figures, leaderless, are lying in wait to fuck a life up, as a form of entertainment, in the name of Anonymous, and the Nothing that it stands for.
While sorting through the ruins, those who still have not looked away from the trainwreck, who inexplicably still have the energy – the last people to care, and knowing they won’t get a proper response – will invariably raise their eyes and lean in anyway, if only to ask: Why? Why hurt? Why so much pain?
we did it all for the lulz