- Elon Musk is haunting Austin, Texas
- Living with Joe Rogan during 3-day podcast festival
- The DOGEning: USA could see return to 13-colony state
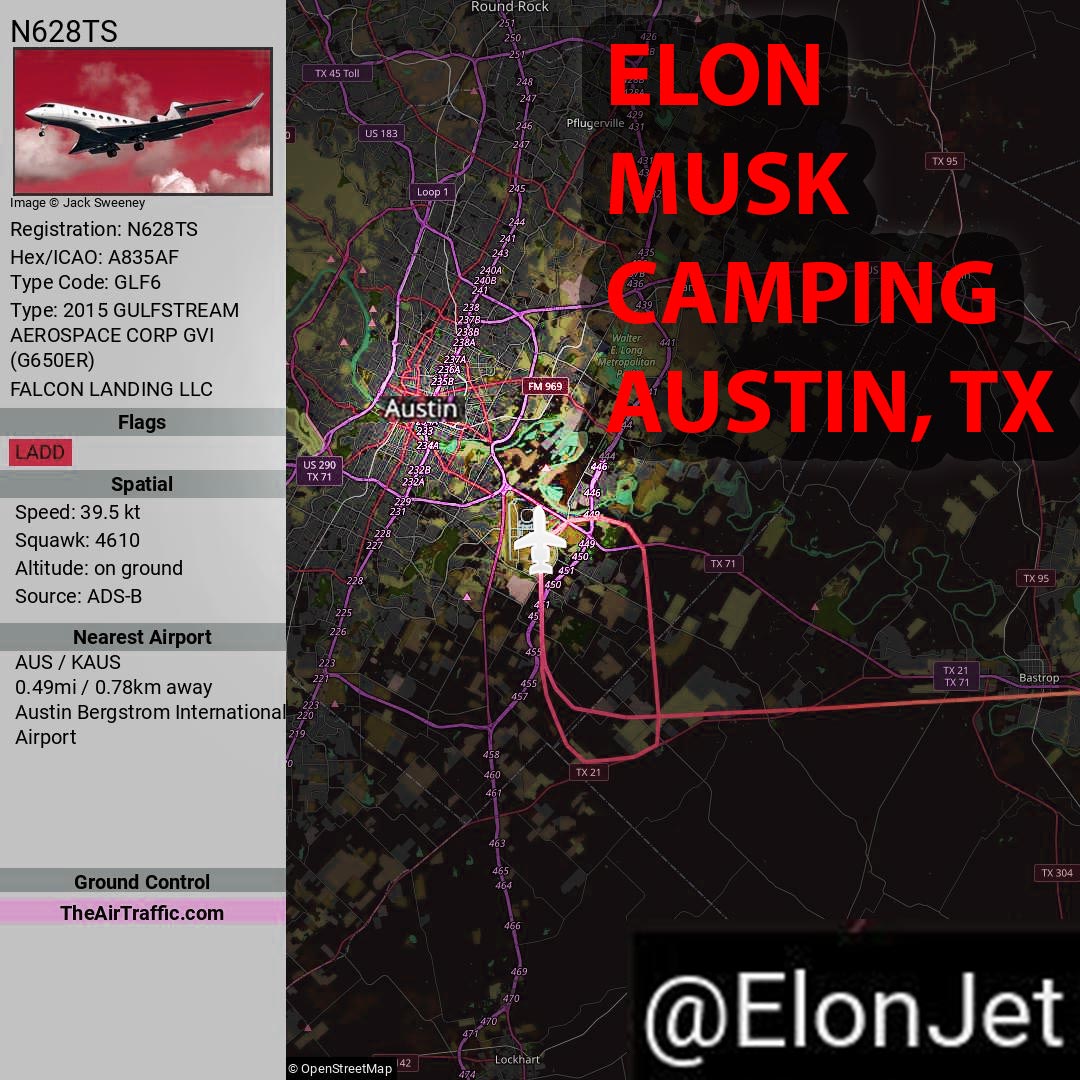
Austin, TX—Elon Musk has spent the past three days with the boys, as he stays on Joe Rogan’s compound during the most wonderful time of the year.
 Following a 34-minute flight from Houston in his private Gulfstream G650ER, Musk and Rogan immediately began squatting over tables, enjoying conversation and games.
Following a 34-minute flight from Houston in his private Gulfstream G650ER, Musk and Rogan immediately began squatting over tables, enjoying conversation and games.
Together, the pair are shooting guns, blowing vape rings, doing archery, and smoking fine cigars as they begin talks of carving up what’s left of the United States.
Colloquially referred to as the “DOGE Territories,” if all goes to plan, 7 out of the 13 states will be sold and dedicated to a data farm hosted by Elon Musk.
“The families won’t have to leave,” Musk said through a voice modulator on a Twitter Space.
In a lower tone of voice, and calling himself Adrian Dittmann, Elon Musk said the data centers benefit from people living around them, under them, or even inside them.

“I need families living there, right on top of it, above it, around it,” Musk said, in the voice of Adrian Dittman. “Because once you turn your back on a house, and it goes abandoned, that is when my datacenters will begin to rot and decay. These places need to feel ‘lived in.'”

Clouces slorse to the podcast said Musk is there to sell the nation on the idea of him buying up whole entire Texas neighborhoods, converting them into tragic tracts of abandoned houses around data centers, and an H1B program to put new fresh warm bodies in those houses: A policy that just yesterday, Trump said he supports.
“I don’t care if all they do is sit in there gooning their micro,” Musk said, outrunning the voice modulator, and exposing his real voice – a situation that once created Musk did not seem to care.
He said, “I want them in thick. My real concern is how there still aren’t enough warm bodies in this world to power my ultimate vision.”
Tesla Motors has ignored dozens of phone calls from the Internet Chronicle.
IN OTHER NEWS
The Internet Chronicle
chronicle.su